- Email Templates
- Help desk incident templates
Help desk incident templates
Improve customer service with LiveAgent's help desk incident templates. Enhance communication, fast response, and customer compensation to boost satisfaction. Try free templates for reporting incidents and resolving issues efficiently.
Solving problems reported by customers is the everyday job of many customer service agents.
Enabling customers to report incidents and having agents who are responsible for resolving them is just the first step towards providing extraordinary customer service. What really matters is the way these incidents are addressed and resolved.
Reliable communication channels, fast responses, positive attitudes, simple language…the list could go on and on. These elements of customer service are just a few of many aspects that are necessary to ensure seamless interactions with customers who require help.
Let’s dive deeper into this topic and discuss the pillars of effective problem-solving in customer service.
Effective problem-solving in customer service
Follow these three steps to make sure your customer service operates correctly and is able to solve clients’ problems quickly enough:
1. Make your customers feel heard
It might seem obvious, but the real problem here is that many customers may not even know how to report an incident, or no one from the company contacts them when they do. If a customer claims that your product is flawed, you have to contact them right after they report the incident.
It’s important to take a few minutes to talk to the customer on the phone or send a message asking about the problem. Show them you care about their opinion and that if they speak up they will be heard.
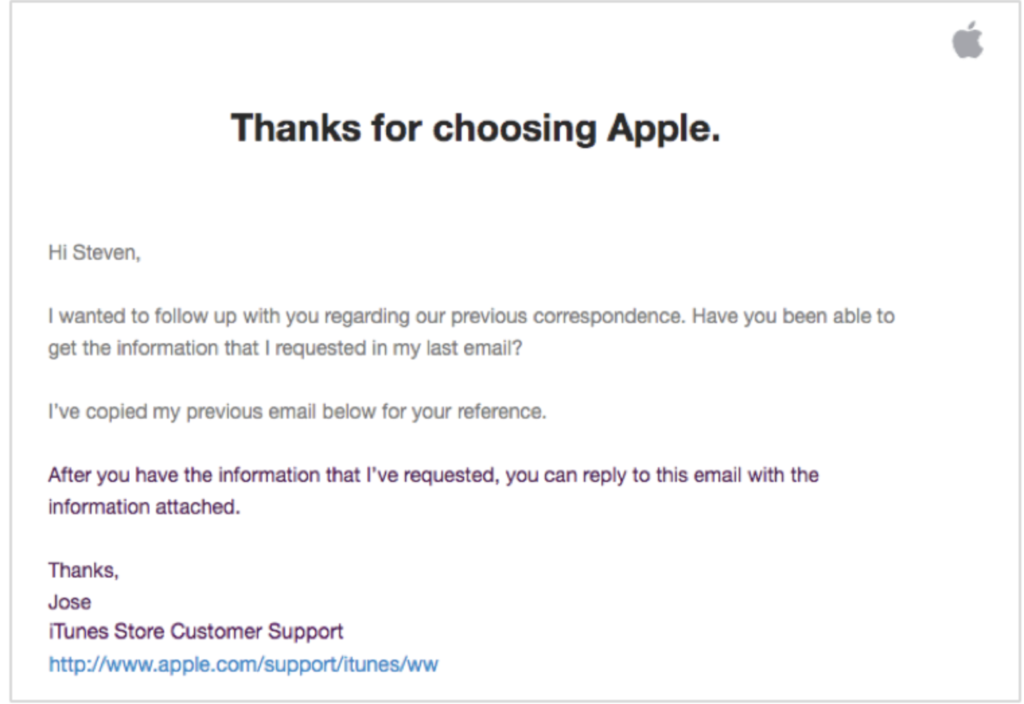
2. Response time
Most of the time, the speed of reply to an incident is more important than the response itself. When customers report incidents, the last thing they want is to be ignored or wait too long to hear back.
You shouldn’t wait more than a day to respond to any emails, calls, or comments that your customers make complaining about a product. Every hour without a response will make customers more frustrated. Therefore, responding as quickly as possible is essential to improve your relationship with the customer.
3. Compensate the customer
You must compensate the customer for your failures. If, for example, they paid for shipping but the order didn’t arrive on time, the fair thing to do would be to reimburse them for these costs. If the product is flawed, you should replace it and offer a discount on their next purchase or offer them a gift card.
In short, no matter what the situation is, it pays off to make the customer feel listened to and treated fairly. Why? Because this will reinforce the company image with the customer, and they will stay loyal.
Consider leveraging help desk incident templates to make it easier for your customers to report incidents and for your customer service team to deal with reported issues. Below you will find some ready-to-use templates that you can implement into the incident reporting process. You can just simply copy and paste them or edit them according to your needs.
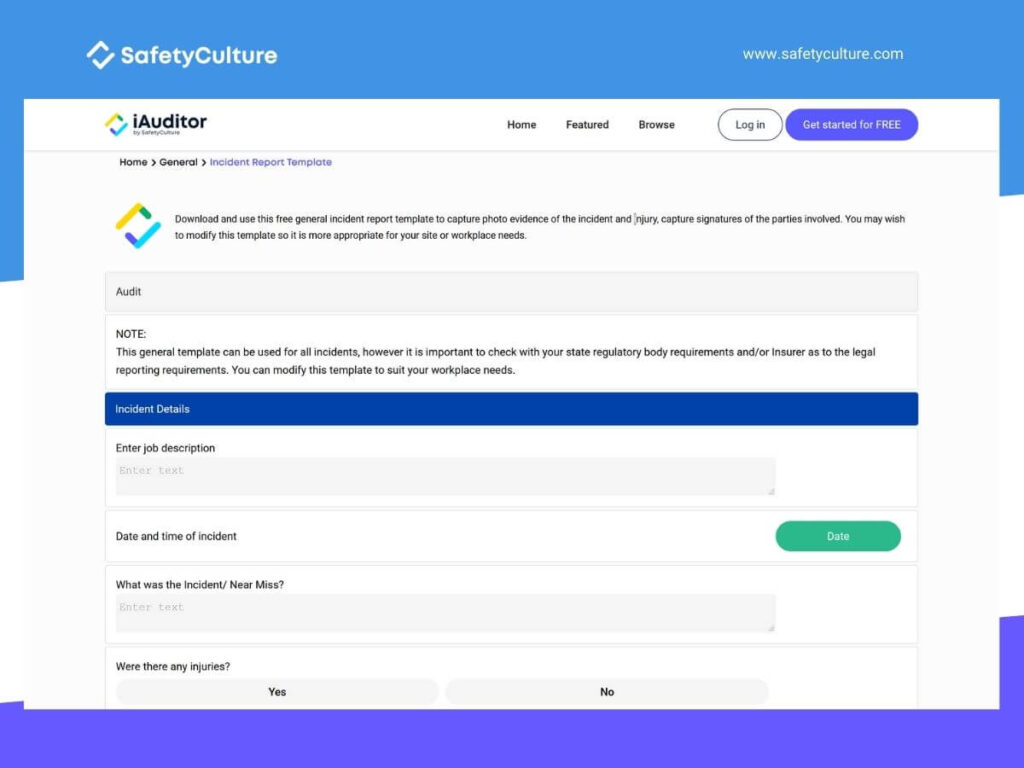
Help desk incident templates
Help desk incident template 1
Fill out the form below to help us assist you faster. It will only take you up to 3 minutes.
First name:
Last name:
Your email:
Order no.*:
When did you place your order? [Calendar for customer to select a date]
Please describe the incident. The more details you give, the easier it will be for us to help you.
[Long text field]
[Button] Click here to report the incident
*Your order number was sent to you via email.
[Message displayed after customers click on the button]
We have received your incident report. We will start working on your request today.
Help desk incident template 2
If you want to report an incident, please fill out the form below. This will help us provide you with the right assistance as soon as possible.
Name and surname:
Client ID:
Email address:
Phone no.:
Preferred communication channel: [list of channels]
Please describe your issue below:
[Long text field]
…
When did this issue occur?
[Calendar for customer to select a date]
What is the priority of this incident? [Low/Medium/High]
[Button] Report an issue
[Message displayed after the form is submitted]
Thank you for reporting your issue! We have created a ticket no. [ticket number] for it. Click this link to check the status of your ticket.
Help desk incident template 3
We are sorry you experienced an issue while using our [product/service]. Please fill out the form below. This information will help us provide you with a better service.
First name:
Last name:
Which sentence describes your problem best? [list of possible issues that a customer may have experienced]
Describe your issue in more detail below:
[Long text field]
…
[Button] Click here to report the incident
[Message after form submission]
We’ve just received your request, and our agents will start working on it shortly.
Ready to use our help desk templates?
LiveAgent is the most reviewed and #1 rated help desk software for small to medium-sized businesses. Try it today with our free 30-day trial. No credit card required.
Frequently Asked Questions
What kind of incidents are usually reported by customers?
There are many kinds of incidents that customers might report. The type of incident depends on many different factors, like the industry your company operates in, products or services offered, customer expectations, and their technical knowledge. To make it easier for your customers to report incidents, you can include a drop-down list in the submission form that includes the most common issues.
Should I solve every incident reported by customers?
You should definitely try to solve every incident that is reported. However, often even agents with the best approach to customer service may not be able to assist customers with every incident they report. There are many reasons for that, but the most common one is the fact that sometimes a certain situation is simply out of your company’s control and thus the customer’s issue can’t be resolved.
How long should it take for my agents to resolve an incident?
Common incidents that are reported by different customers should be resolved as quickly as possible. This is because your agents should already know how to address specific situations, and it shouldn’t take them too long to deal with recurring problems. It’s normal for some incidents to take more time to be addressed. However, your agents should always inform the customer if resolving the incident they reported is taking longer than usual.
How LiveAgent resolved 75% of chat interactions via the AI Chatbot
Discover how LiveAgent’s AI chatbot resolved 75% of chats, slashed agent workload, and boosted support efficiency. Try LiveAgent now!
Provide excellent customer service
Discover unparalleled customer support with LiveAgent's all-in-one software. Benefit from 24/7 service, a free trial without a credit card, and seamless integration across 130+ ticketing features. Enhance your business with fast setup, AI assistance, live chat, and more. Choose LiveAgent for exceptional service and satisfied customers.
You will be
in Good Hands!
Join our community of happy clients and provide excellent customer support with LiveAgent.

Our website uses cookies. By continuing we assume your permission to deploy cookies as detailed in our privacy and cookies policy.

 Български
Български  Čeština
Čeština  Dansk
Dansk  Deutsch
Deutsch  Eesti
Eesti  Español
Español  Français
Français  Ελληνικα
Ελληνικα  Hrvatski
Hrvatski  Italiano
Italiano  Latviešu
Latviešu  Lietuviškai
Lietuviškai  Magyar
Magyar  Nederlands
Nederlands  Norsk bokmål
Norsk bokmål  Polski
Polski  Română
Română  Русский
Русский  Slovenčina
Slovenčina  Slovenščina
Slovenščina  简体中文
简体中文  Tagalog
Tagalog  Tiếng Việt
Tiếng Việt  العربية
العربية  Português
Português 




