What is a password validator?
A password validator determines whether a proposed password is acceptable to use. To determine if the password is acceptable, the validator runs a series of checks ensuring it meets minimum length requirements, has a variety of characters, or hasn’t been used previously. Password validators can also determine whether the proposed password was found in data breaches and leaks.
How do password validators work?
Password validators have a built-in fraud protection setting that defines the minimum level a password needs to meet before being accepted. This level could be the minimum number of characters, character variety, or a combination of both.
Generally, password validators visualize the proposed password strength as the user is typing in their password. All passwords start out as weak (red color), and as the user adds more character variety or more length, the password eventually becomes strong (green).
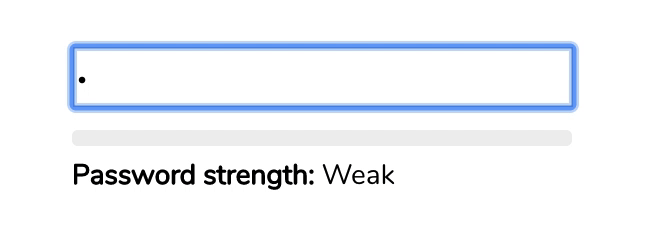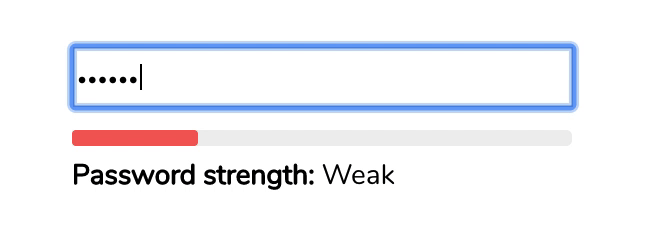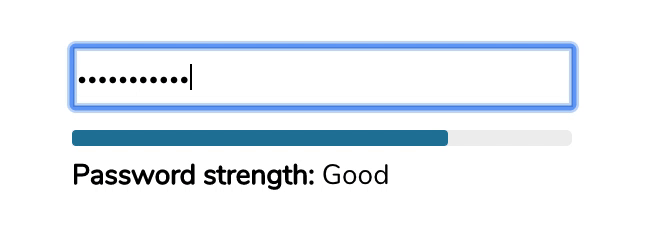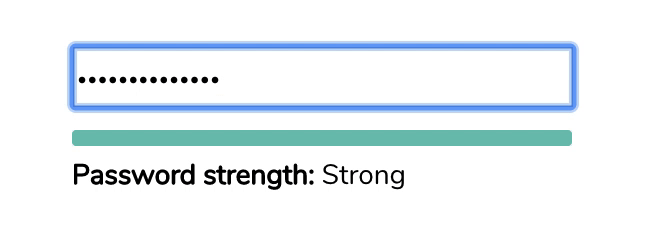
What does the LiveAgent password validator do?
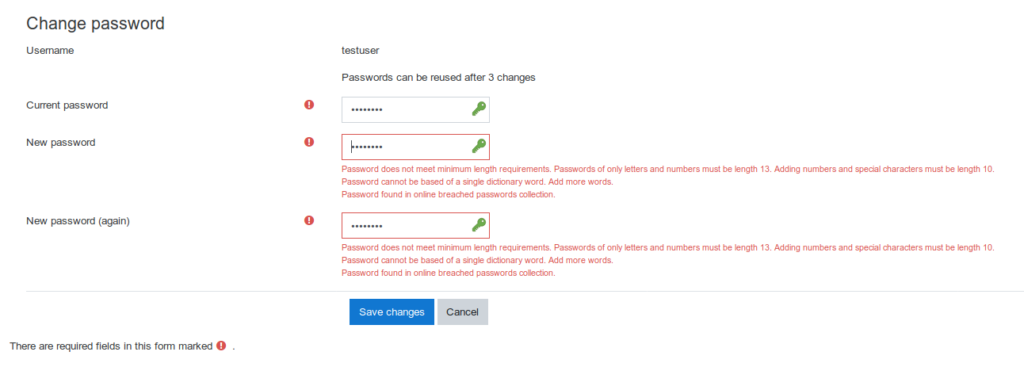
The LiveAgent password validator will not let you choose a weak password. It will force you to use a password that is strong and hasn’t been used previously. If you choose a weak password, you’ll see an error message that will prompt you to improve your password quality and provide suggestions on how to do so.
The LiveAgent password validator will also let you know if your proposed password was leaked or associated with any data breaches.
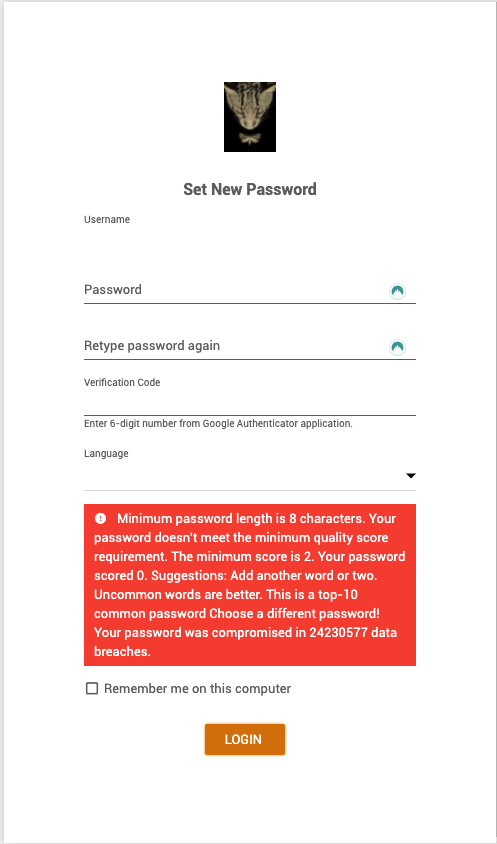
What is a strong password?
To build a strong password, ensure your proposed password:
- Has between 8-15 characters
- Contains at least one uppercase letter and one lowercase letter
- Contains at least one numeric digit
- Contains at least one special character (for example: @!?=]<)
How is a password validator beneficial?
A password validator is beneficial because it ensures your passwords are strong and less likely to be guessed or compromised. Remember, a strong password keeps your data safe and prevents hackers from stealing sensitive information. By protecting your information and having unique, strong passwords on all websites, you’re ensuring that:
- Hackers won’t steal your identity
- Your credit card and bank information is secure
- Your other accounts won’t be compromised
- Hackers won’t blackmail you
- You won’t put your family, employer, or clients in danger
How can I remember complex passwords?
Strong passwords are often random strings of characters and numbers, making them hard to remember. It can be tempting to write down your passwords on a piece of paper or your phone Notes. However, this isn’t advisable. For example, you can easily lose the piece of paper, or someone can get a hold of it. The same goes for writing down passwords on your phone. Just like computers, phones can be hacked. If your phone is in the wrong hands, your identity and bank account can be at stake.
The best way to store complex passwords is inside of password managers. Password managers are paid software applications that can store passwords, credit card numbers, and other sensitive information. They’re protected by a master password that needs to be strong and unique, and you should be able to memorize.
A few examples of password manager applications are:
- LastPass
- Keeper
- Dashlane
- 1Password
- PasswordBoss
- NordPass by NordVPN
Google also offers a free password manager that showcases which of your saved passwords are found in existing data breaches.
Want a secure help desk for you and your customers? Look no further!
What can I do if I suspect malicious activity or suspect my LiveAgent account was compromised?
If you suspect that your LiveAgent account has been compromised, the best way to move forward is to review your account security which you can do in the LiveAgent password audit log. You can then determine if a hacker locked one of your agents out of their accounts. The next step is to request all users to change their passwords and ensure that everyone has 2-factor authentication enabled.
What is a password audit log?
The LiveAgent password audit log records each password change made by your users. Admins and account owners can see the date and time each agent updated their password.
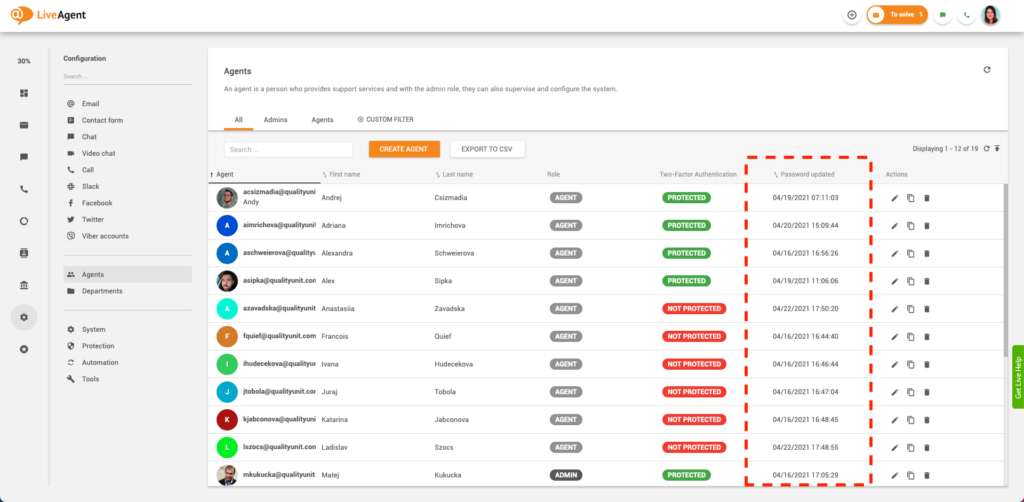
Where can I find the LiveAgent password audit log?
- Log in to LiveAgent
- Click on Configuration
- Click on Agents
- Find the 6th column titled “Password updated”
Knowledge base resources
- LiveAgent security policy
- Content security policy
- General protection settings
- How to define password requirements
- Ban IPs
Ready to secure your help desk?
Keep your client’s data secure with password validators, 2-factor authentication, and our password audit log. Try LiveAgent today with a free 30-day trial. No credit card required.
Concerned about the security of your customer accounts?
Enhance your security, prevent unauthorized access, and build trust with LiveAgent's Password Validator feature.
Frequently Asked Questions
What is a password validator?
A password validator determines whether a proposed password is acceptable to use. To determine if the password is acceptable, the validator runs a series of checks ensuring it meets minimum length requirements, has a variety of characters, or hasn’t been used previously. Password validators can also determine whether they found the proposed password in previous data breaches and leaks.
How do password validators work?
Password validators have a built-in fraud protection setting that defines the minimum level a password needs to meet before being accepted. This level could be the minimum number of characters, character variety, or a combination of both.
What is a password audit log?
The LiveAgent password audit log records each password change made by your users. Admins and account owners can see the date and time each agent updated their password.
LiveAgent monthly updates: May edition
Discover LiveAgent’s May updates: Blind transfer calls, enhanced ticket actions, better email sorting, security fixes & more—read now!

 Български
Български  Čeština
Čeština  Dansk
Dansk  Deutsch
Deutsch  Eesti
Eesti  Español
Español  Français
Français  Ελληνικα
Ελληνικα  Hrvatski
Hrvatski  Italiano
Italiano  Latviešu
Latviešu  Lietuviškai
Lietuviškai  Magyar
Magyar  Nederlands
Nederlands  Norsk bokmål
Norsk bokmål  Polski
Polski  Română
Română  Русский
Русский  Slovenčina
Slovenčina  Slovenščina
Slovenščina  简体中文
简体中文  Tagalog
Tagalog  Tiếng Việt
Tiếng Việt  العربية
العربية  Português
Português