- All checklists
- Call Center
- Call center compliance checklist
Call center compliance checklist
A call center compliance checklist ensures adherence to regulations and data protection. Key measures include building secure networks, managing vulnerabilities, protecting cardholder data, implementing encryption, access control, and regular network monitoring.

- Build and sustain a secure network infrastructure
- Develop a vulnerability management program
- Protect cardholders’ data
- Put an information security policy in place
- Implement strong access control measures with LiveAgent
- Provide voice transactions with encryption
- Prevent access to payment information
- Don’t write down sensitive information
- Minimize the use of mobile devices in the workspace
- Regularly monitor and test networks
As a business owner, you will know the importance of compliance with applicable laws and regulations. Call centers that keep many sensitive customer records are especially at risk. How to maximize help desk security?
Here’s how: by following a handy checklist of call center compliance requirements. By completing it, you will help keep your call center safe.
The importance of a call center compliance checklist
It’s a tool that helps all kinds of contact centers to stay up-to-date with the latest legal requirements. By ensuring that your agents adhere to the rules listed below, you can reduce the risk of fines or other penalties.
Who can benefit from a call center compliance checklist?
- call center agents
- business owners
- call center supervisors
A call center compliance checklist can be used by businesses of all sizes. Our checklist will help your business obey the law whether it is a small one with a single contact center or an enterprise with multiple call centers.
Explore the call center compliance checklist
This is the backbone of your compliance program. Without a secure network, all of your call center’s operations are open to danger.
Why is it important to build and sustain a secure network?
Because it helps protect your customer data from unauthorized access, theft, or modification.
How to build and sustain a secure network infrastructure?
If you’re not sure where to start, consider working with an IT security consultant. It can be done in two ways:
- by implementing firewalls that monitor network traffic, detect threats to protect internal networks by comparing your traffic to a list of standards
- by avoiding the use of default access passwords, which can dramatically increase the chances of a data breach
Tip: for more information on building and sustaining a secure network infrastructure, consult the National Institute of Standards and Technology (NIST).

Which tools to use for building and sustaining a secure network?
- firewalls
- intrusion detection systems
- password management software
- VPN
- anti-virus software
Web services are heavily subjected to malware targeting. Credit card transactions are not an exception, so contact centers also need to be protected against those. The development of such a program is a proactive approach to managing cyber threats and vulnerabilities.
Why is it important to develop a vulnerability management program?
It helps you identify, prioritize, and remediate security issues before they become problems for your business or customers. Such a program can also tell you exactly what you need to do in case of a security breach.
What are the key components of a vulnerability management program?
- Inventory of network hosts and Internet-facing assets – network security begins by knowing what is in your system, how it works, and why it needs protection. It’s also important to check if there are any unknown or unauthorized devices on your network that can pose a risk. For example, a computer that is not in your network inventory could be used for an attack.
- Protocols and procedures – a program should contain a set of protocols and procedures to follow in case of security issues or breaches. For instance, if someone steals credit card data from your system, you must establish a protocol that will prevent the theft from affecting your business.
- Vulnerability scan – conducted to identify potential security risks. They can be manual or automated and they should be performed at least once per month.
- Remediation plan – once you discover vulnerabilities in your system, you have to develop a remediation plan for how you’ll fix the issues that were found.
- Patch management – systems need protection against newly discovered vulnerabilities. You must have compliance processes for deploying patches and updates in a timely manner.
- Education and awareness – employees are your first line of defense, so they need to be aware of threats and how to protect against them.
Which tools to use for developing a vulnerability management program?
- vulnerability scanners
- patch management software to automatically update patches
- software programs to monitor and analyze logs of network activity for unusual, suspicious, or risky behavior (SIEM)
- mobile device management tool e.g. smartphones and tablets
- intrusion detection systems (IDS) for detecting network intrusions and responding to them appropriately
Protected access to cardholder data refers to any information about a customer that’s stored on your system. This can include names, addresses, phone numbers, credit card numbers, and more.
Why is it important to protect cardholders’ data?
It prevents hackers from gaining access to cardholder information and using it to commit fraud or identity theft. Additionally, it prevents any unauthorized transmission of cardholder data.
How to protect cardholders’ data?
First, make sure you’re compliant with The Payment Card Industry Data Security Standard (PCI DSS standard) requirements. Then, implement a strong access control measure to protect the private details of your clients.
Tip: avoid storage of customer details and remove any previously kept data.
A powerful cryptographic system and encryption are needed to ensure that sensitive cardholder data is transmitted securely.
Which tools to use for protecting cardholders’ data?
- compliance management platforms (with a built-in vulnerability scanner)
- encryption software
This is a document that outlines an organization’s approach to protecting its electronic information.
Why is it important to put an information security policy in place?
It provides a framework for employees to follow when handling sensitive data and thus helps protect the business.
How to develop an information security policy?
- consult with your legal department to make sure that the policy complies with any applicable laws
- work with your IT department to identify which technologies and procedures will need to be implemented for the IS policy to work as intended.
- make sure that every employee is aware of their responsibilities under this new policy before it goes into effect

Which tools to use for developing an information security policy?
- policy management software to manage your policies and procedures by automating tasks, such as tracking who has access to different documents or storing revisions of all versions ever created
- Legal and Information Technology departments within the organization
- online templates that can help you get started with drafting your own policies and procedures
Access control is a process that lets you manage who has access to your systems and data. Selecting a help desk software that has all of the latest security capabilities is imperative here.
Why is it important to have strong access control measures?
It protects your data from unauthorized access, reduces the risk of internal fraud and abuse, and helps protect customer privacy.
How to implement strong access controls?
The key is to choose automated help desk software such as LiveAgent to control all measures on your behalf. It’s a solution that helps you safely manage all your customer inquiries from one interface.
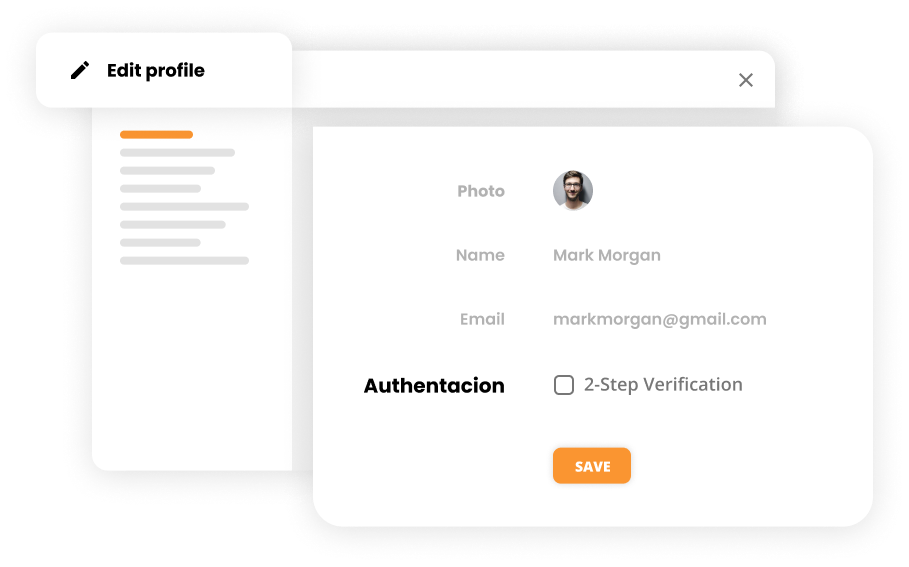
By choosing such a tool, you will increase the security of your customers’ data. LiveAgent provides:
- BAN IPs
- 2-step verification
- HTTPS Encryption
- Multiple Data Centers
- GDPR
You can test LiveAgent out for free before making any financial commitments.
Which tools to use for implementing strong access control measures?
- help desk software with a built-in access control feature (like LiveAgent)
- access management solutions
- call center software
Encryption is a process of converting data into ciphertext so that it can only be accessed by those who have the decryption key.
Why is it important to provide voice transactions with encryption?
Doing so assures customers that information being transmitted is protected from eavesdropping and other forms of interception.
How can voice transactions be encrypted?
There are several different encryption protocols that can be used, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS).
Tip: if you are using LiveAgent’s help desk, you can take advantage of its built-in encryption. LiveAgent encrypts all data by default via SSL (HTTPS) and TLS, so all the traffic between your website/application and our servers is secure.

Which tools to use for providing voice transactions with encryption?
- voice transmission equipment that supports encryption
- strong encryption algorithm
- Voice over Internet Protocol (VoIP) providers and phone systems that use SSL or TLS
To prevent any fraudulent activity, it’s important not to allow access to customer payment information.
Why is it important to prevent access to payment information?
Not allowing access helps protect your customers’ financial details from being stolen by cybercriminals.
How do you prevent payment information from being accessed?
First, make sure your employees are aware of their responsibilities regarding sensitive data protection. Use strong authentication procedures such as two-factor authentication and one-time passwords. Also, encrypt all data transmissions between payment terminals and servers so that no one can intercept them in transit.
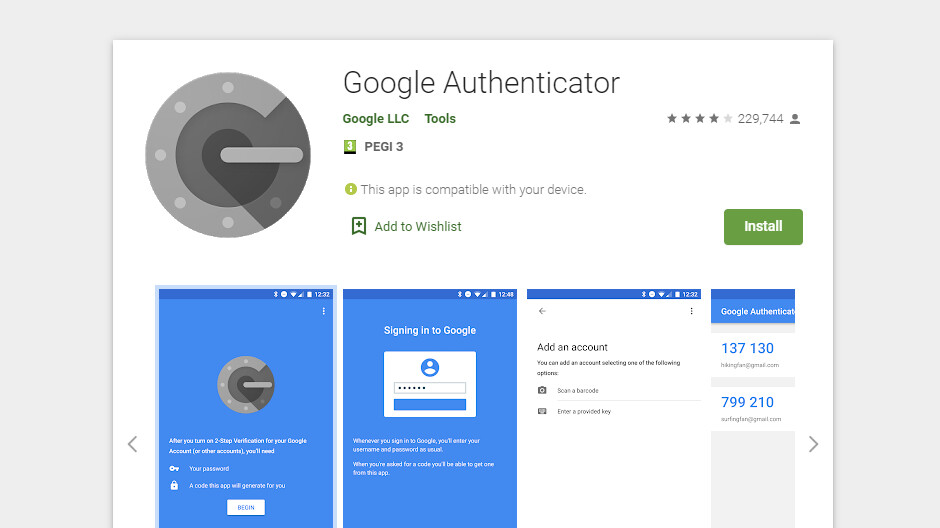
Which tools to use for preventing access to payment information?
- one-time password generators (like Google Authenticator)
- data encryption software (such as OpenSSL) or hardware appliances like VPNs
- data loss prevention (DLP) solutions
If you must keep track of this data, make certain that it is stored in a secure location and that access is limited to authorized personnel only.
Why is it important to not write down sensitive information?
Doing so is not in compliance with GDPR law and makes it easy for unauthorized individuals to access this information.
How can you make notes and stay in compliance with the law?
If you must take notes, make sure to use a secure method of storing them. This could include locking away notebooks in a safe or using an encrypted file storage system.

Which tools to use for keeping track of sensitive information?
- encrypted notepads
- notebook locks
- password-protected files
The use of mobile phones in a contact center increases the risk of data loss or theft.
Why is it important to minimize the use of mobile devices?
It reduces the chances of sensitive information being lost or stolen due to an employee error such as losing their device.
How to minimize the use of mobile devices in the workspace?
Educate your employees on the cyber security risk associated with using a personal device and make sure they understand the importance of data security. Require employees to password-protect their devices and install reputable security apps. Make sure that all sensitive data is encrypted before being stored or transmitted on a mobile device.

Which tools to use for minimizing the use of mobile devices?
- educating employees on data security
- password-protection software
- security apps
- encrypted storage solutions
This is one of the best ways to identify vulnerabilities before they become a problem for your organization or customers.
Why is it important to monitor and test your network?
It helps you prevent unauthorized access, data loss, or theft from hackers who might be trying to get into your system through weaknesses and gaps that haven’t yet been discovered.
How to monitor and test networks?
Install a network security monitoring tool to keep track of all activity. Set up alerts so that you can be notified of any suspicious activity that occurs in real-time. Regularly test the security of your networks by running vulnerability scans and penetration tests.
Which tools to use for monitoring and testing networks?
- network security monitoring tools
- alert systems
- vulnerability scanning software
- penetration testing tools
Common call center safety issues and threats
- Personal data threats
One of the most common dangers in a contact center is the risk of data theft or loss. Agents are privy to a great deal of personal information, including social security numbers, bank account details, and credit card numbers. As such, it’s important that all agents receive adequate employee training on how to safely store and transmit this data.
- Internal threats
Call center agents may pose a risk to the center if they have access to sensitive information and become disgruntled. It’s important to regularly monitor agent activity and to have policies in place that restrict access to certain data.
- Temporary employees
Call centers often employ temporary workers to handle peak volumes or cover for sick employees. It’s important to take steps to ensure that these workers are trained on the center’s policies and procedures and that they understand the risks associated with working in a call center, otherwise they may inadvertently compromise its security.
- Accidental clicks
Sometimes employees click on links or open files that they shouldn’t, leading to the installation of malware or the theft of data. It is essential to have safeguards in place against such mistakes, such as strong password protection and security software.
- An employee with a grudge
An employee with a grudge against the company or another agent can do a great deal of damage. For example, they could leak sensitive data, sabotage systems, or harass other employees. It’s important to monitor employee activity closely and have policies in place to deal with such situations.
- External threats
Hackers and scammers from outside the organization can use phishing or other techniques to try to steal information or install malware on call center computers. The best way to protect against these threats is to implement strong security measures such as firewalls, antivirus software, and spam filters.
Summary of the call center compliance checklist
- Build and sustain a secure network infrastructure
- Develop a vulnerability management program
- Protect cardholders’ data
- Put an information security policy in place
- Implement strong access control measures with LiveAgent
- Provide voice transactions with encryption
- Prevent access to payment information
- Don’t write down sensitive information
- Minimize the use of mobile devices
- Regularly monitor and test networks
Frequently Asked Questions
What is compliance in a call center?
The term ‘compliance’ refers to the adherence of CSRs to specific company policies and procedures during customer interactions.
How long does TCPA consent last?
TCPA consent lasts until a consumer revokes it or the company in question discontinues the relevant marketing campaign.
How can I improve my call center compliance?
To improve contact center compliance, you should implement proper agent training in your company, supervise employees’ work, and conduct regular NPS surveys. Also, update policies regularly to ensure that all CSRs are aware of the most current compliance requirements.
What is the difference between DNC and TCPA?
DNC (Do Not Call) regulations prohibit telemarketing calls to residential customers who have registered their numbers on the national DNC list. TCPA (Telephone Consumer Protection Act) regulations protect consumers from unsolicited marketing calls and text messages.
What are compliance questions?
Compliance questions are specific inquiries that agents may be asked to verify the authenticity of a customer or an order. For example, a CSR may ask for a customer’s date of birth or social security number to verify their identity.
Why is call center compliance Important?
It ensures that agents provide accurate and consistent information to customers. It also helps protect CSRs from liability if they provide incorrect or misleading information during customer interactions.
You will be
in Good Hands!
Join our community of happy clients and provide excellent customer support with LiveAgent.

Our website uses cookies. By continuing we assume your permission to deploy cookies as detailed in our privacy and cookies policy.
Want to improve your customer service?
Answer more tickets with our all-in-one help desk software. Try LiveAgent for 30 days with no credit card required.

Hello, I’m Andrej. We’re thrilled to invite you to an exclusive software demo where we’ll showcase our product and how it can transform your customer care. Learn how to achieve your business goals with LiveAgent or feel free to explore the best help desk software by yourself with no fee or credit card requirement.
Andrej Saxon | LiveAgent support team
- How to achieve your business goals with LiveAgent
- Tour of the LiveAgent so you can get an idea of how it works
- Answers to any questions you may have about LiveAgent

 Български
Български  Čeština
Čeština  Dansk
Dansk  Deutsch
Deutsch  Eesti
Eesti  Español
Español  Ελληνικα
Ελληνικα  Hrvatski
Hrvatski  Italiano
Italiano  Latviešu
Latviešu  Lietuviškai
Lietuviškai  Magyar
Magyar  Nederlands
Nederlands  Norsk bokmål
Norsk bokmål  Polski
Polski  Română
Română  Русский
Русский  Slovenčina
Slovenčina  Slovenščina
Slovenščina  简体中文
简体中文  Tagalog
Tagalog  Tiếng Việt
Tiếng Việt  العربية
العربية  Português
Português 

